 Greeting from Felix
Greeting from Felix
Shift Security Left #7
Hey! A fortnight just flew by, and here I am! Hope you have a nice Saturday reading my nice newsletter :)
If you like what I post and it feels like you have related materials to share with our growing security-aware community, just drop me a line (find a link in the footer) or vote for Shift Security Left on Hackernoon Noonies'22.
Real world

Wi-Fi spy drones used to snoop on financial firm
Fintech, supply chain or critical third-party software suppliers, check the roof for parked or hovering drones now and again.
Here's a story of a Phantom drone, carrying a network-intrusion kit, which landed on the roof to target the financial company's internal devices.
Secure Architecture
SOK: On the analysis of web browser security
Modern web browsers are too complex to be bug-free, right? In this paper written by 9 authors, you'll find a systematised view on the browser security landscape—with popular classes of security bugs, their exploitation techniques, and deployed defences uncovered.
This paper is useful for everyone working on complex software.
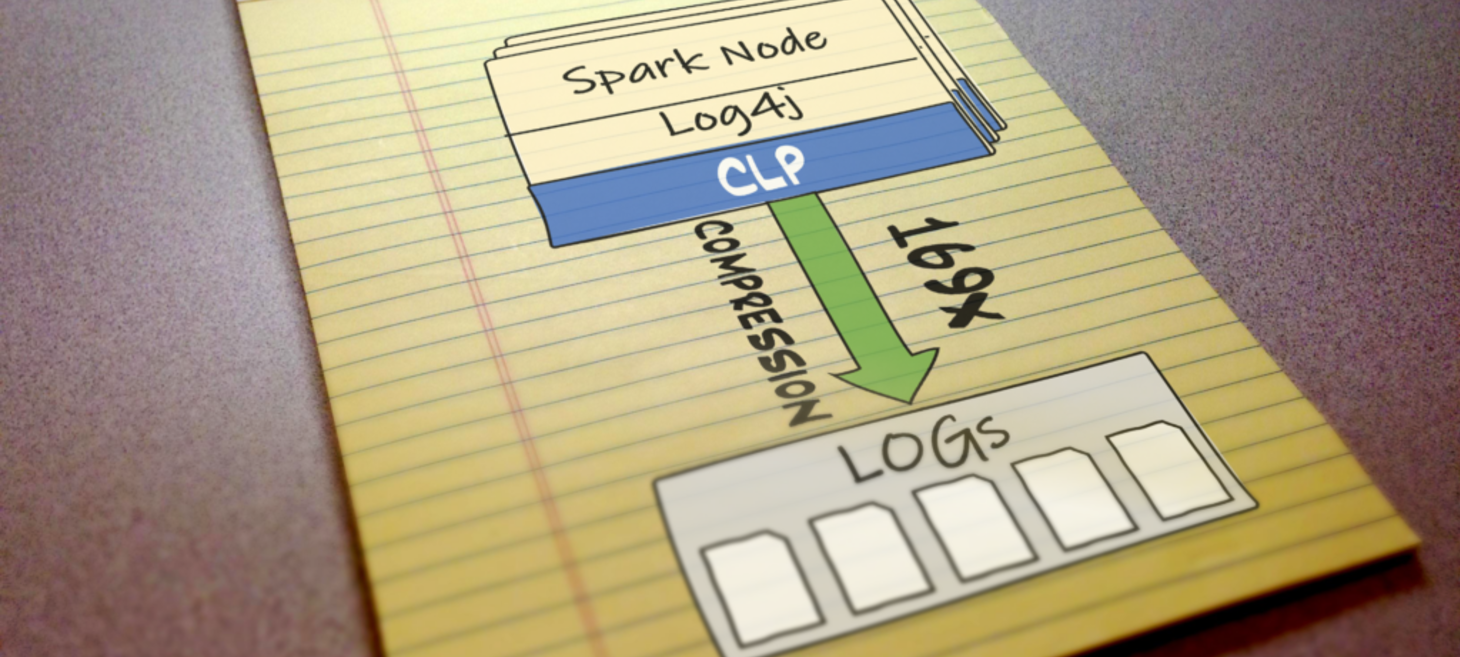
Reducing logging cost by two orders of magnitude using CLP
Imagine you work at Uber. The business grows rapidly, the amount of data being logged also increases dramatically. What you can do with it? Read an explanation by Jack (Yu) Luo and Devesh Agrawal.
Basically, each unstructured log message is parsed into template + variables (like creating an SQL query with parameters, but in reverse) and then stored in a table that is later compressed by column.
They also use a few tricks to decrease storage size: as timestamps are always increasing, you can only store deltas; as most variables will repeat, so you can store actual values in a dictionary on the side and only reference ids in the logs table, etc.
Find more tricks in the article.
Cryptography

The race to native code execution in PLCs: Using RCE to uncover Siemens SIMATIC S7-1200/1500 hardcoded cryptographic keys
Long time ago, Siemens introduced asymmetric cryptography into the integrated security architecture of its TIA Portal v12 and SIMATIC S7-1200/1500 PLC CPU firmware families. Team82 uncovered and disclosed to Siemens a new technique targeting these PLC CPUs and enabling to recover a global hardcoded cryptographic key (CVE-2022-38465) used by each Siemens affected product line.
The key, if extracted by an attacker, would give them full control over every PLC per affected Siemens product line. Wow
Vulnerabilities
Browser-powered desync attacks: A new frontier in HTTP Request Smuggling
HTTP handling anomalies cover the sequence of novel vulnerabilities and attack techniques that led to discovery of browser-powered desync attacks. This research, presented at Black Hat USA 2022 and DEF CON 30, shows how to turn victim's web browser into a desync delivery platform.
Your Amiibo’s haunted: Exploiting Flipper Zero’s NFC file loader
This article demonstrates a buffer overflow in Flipper Zero’s NFC file loader: an open-source and customizable "multi-tool for pentesters and geeks in a toy-like body". The device comes with several built-in applications to transmit and receive sub-1GHz frequencies, such as RFID, NFC, and Bluetooth. Well, hacker tools have code, too, and the code has vulnerabilities! :)

